Free Remote IoT Access On Mac: No Port Forwarding Guide
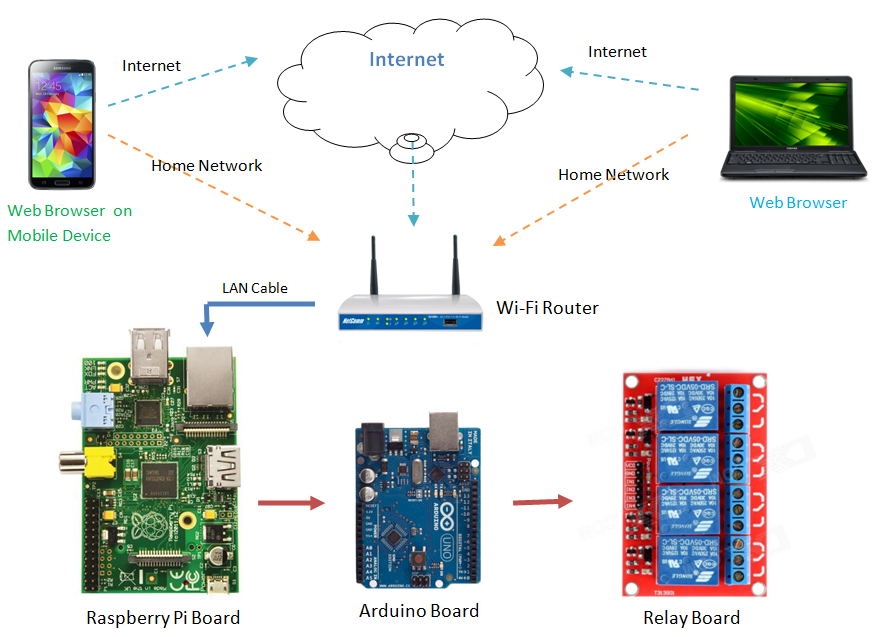
Are you wrestling with the challenge of accessing your Internet of Things (IoT) devices remotely, particularly when they're tucked behind the protective walls of a router or firewall? The ability to remotely control and monitor your IoT devices, whether they're Raspberry Pis, home automation systems, or industrial sensors, is not just a convenience; it's a necessity in today's interconnected world.
The inherent difficulty lies in the fact that these devices often reside on private networks, shielded from direct access from the outside world. Standard methods like port forwarding, while effective, can be complex to configure and pose security risks. This is where understanding alternative, secure, and often free, approaches becomes invaluable. This guide aims to demystify the process, providing practical solutions and insights to empower you to take control of your IoT devices from anywhere.
The cornerstone of remote access often hinges on understanding the intricacies of network address translation (NAT) and firewalls. Your IoT devices typically receive private IP addresses from your router, making them invisible to the broader internet. Port forwarding, a common solution, manually directs incoming traffic from specific ports on your router to the internal IP addresses of your IoT devices. However, this method demands careful configuration and can create vulnerabilities if not handled with utmost precision. Thankfully, there are innovative methods that bypass the need for port forwarding, offering a more secure and user-friendly experience. These methods often involve intermediary services that act as a bridge, allowing you to establish a secure connection without exposing your devices directly to the internet. The advantage of such an approach is twofold: it simplifies the setup process and minimizes the potential for security breaches.
The initial phase focuses on establishing remote access to the cellular router itself. This preliminary step is fundamental, as it grants you the ability to monitor and configure the router remotely. Depending on the router model, this can be achieved through a web interface or, in some cases, through a command-line interface (CLI) accessed via SSH. The specific steps to achieve this vary, but common practices involve setting up a static IP address for your IoT device, configuring the routers firewall, and enabling remote management access. In parallel, remote SSH access, if supported by your device, can also be very helpful. This feature permits you to interact with your device using SSH, allowing you to execute commands, manage files, and troubleshoot issues directly.
One of the key tools to consider is remote.it. This software provides a straightforward method for establishing remote connections to your IoT devices. Installing the remote.it software on your endpoints (the devices you want to access) enables secure, encrypted connections. If, for any reason, remote.it cannot be installed directly on your device, alternative connection types are available, providing flexibility across different hardware and software environments.
For instance, let's consider the Raspberry Pi, a popular choice for IoT projects. After setting up the device and connecting it to your network, the next step is to install the remote.it software. This process involves downloading the appropriate software package from the remote.it website and following the installation instructions specific to your operating system. Once installed, you'll need to register your device with the remote.it service and configure the necessary settings for remote access. The software facilitates secure connections, allowing you to securely access your Raspberry Pi remotely.
In many cases, the core question revolves around gaining remote access without the need to configure port forwarding on your router. Various services provide solutions for this challenge. These services often utilize techniques like reverse tunneling or proxying to establish a secure connection between your device and the remote access platform. By using these intermediary services, you effectively bypass the need to directly expose your device to the internet, significantly reducing the risks associated with port forwarding.
Pinggy is another tool, which provides remote SSH access. By using Pinggy, you can create a secure tunnel for your SSH traffic. This approach allows you to access your device without complex network configurations. Another tool, such as SocketXP, also offers a solution for remote SSH access. By setting up a SocketXP agent on your IoT device, you can establish a secure and reliable connection to your device from anywhere.
When it comes to software, security should always be a top priority. Ensure that you download software from reputable sources and verify its integrity before installation. Take steps like checking for digital signatures or verifying the source code to confirm that the software has not been tampered with. Furthermore, maintain the practice of regularly updating your software to patch security vulnerabilities. This proactive approach reduces the risk of unauthorized access and ensures the safety of your devices and data.
The following table provides a summary of the key steps required for setting up remote access to a Raspberry Pi or other IoT device. These steps offer a concise overview of the procedures involved, from initial device setup to installing and configuring remote access software. Following these steps will streamline the process and make it easier to take control of your IoT devices.
| Step | Description |
|---|---|
| 1 | Install remote.it on the target device. |
| 2 | Download and install the socketxp iot agent or similar software if remote.it is not an option. |
| 3 | Configure the device's network settings, ensuring a stable internet connection. |
| 4 | Register your device with the chosen remote access service (e.g., remote.it, SocketXP). |
| 5 | Configure the remote access settings within the chosen service to specify the services you want to access (e.g., SSH). |
| 6 | Test the remote access connection from another device or network. |
For those seeking to control their devices, many guides and resources are available. These resources will help you understand the different methods, tools, and technologies. With the help of these guides and options you can ensure that you set up remote access securely.
Remember that, even with secure tools, responsible usage and security awareness are critical. Always keep your devices updated with the latest security patches and use strong, unique passwords to prevent unauthorized access. Consider enabling two-factor authentication whenever possible. Additionally, regularly review your network and device configurations to ensure they meet your security needs.
Another approach involves running a web application directly on your IoT device. By installing and running a web application, you can create a web interface that allows you to remotely connect and control your IoT system via a web browser. This provides a user-friendly way to manage your devices from any device with an internet connection. This method is effective for IoT devices, since it provides a consistent user interface.
Tools like the Tor browser can also be beneficial for accessing your IoT devices. Tor provides an extra layer of security and privacy, allowing you to bypass network restrictions. This approach can be useful if your home network has blocked access to certain resources. The browser encrypts and bounces traffic through various nodes, adding an extra layer of security.
The process of remote access can be tricky. But by using the right tools and following the correct procedures, it can become much easier. This guide breaks down everything that you need to know about connecting your IoT devices behind a firewall. From understanding the fundamentals of network security to utilizing innovative tools, this guide gives you the necessary knowledge to remotely control your IoT devices. With the combination of the right tools and understanding the security steps you can take control of your devices from almost anywhere.